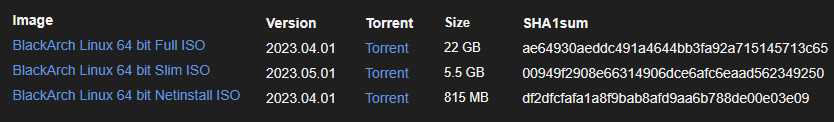
BlackArch Linux
BlackArch Linux is a powerful, Arch Linux-based distribution tailored for professional penetration testers, red teamers, ethical hackers, and advanced security researchers. Known for its extensive toolkit, BlackArch includes over 2,800 pre-installed security tools, all neatly organized into categories such as exploitation, forensics, reverse engineering, wireless analysis, fuzzing, malware research, and cryptography. Its focus on minimalism and efficiency makes it ideal for users who value performance, customization, and full control over their testing environment.
Unlike beginner-friendly distros, BlackArch is designed for those with a solid understanding of Linux and command-line operations. It adheres to Arch Linux's rolling release model, meaning users always have access to the latest kernel updates and security packages without needing to reinstall the system. BlackArch can be used as a standalone distribution or layered on top of an existing Arch installation, allowing for modular integration of tools as needed.
The distribution supports multiple lightweight window managers such as i3, Openbox, and Fluxbox, giving users flexibility over their user interface while minimizing resource usage—critical for virtual machines, older hardware, or portable hacking rigs. It also offers ARM architecture support, including builds for Raspberry Pi, making it an excellent option for building portable pentesting kits or IoT security labs.
While not as widely marketed as Kali Linux or Parrot OS, BlackArch is favored in the infosec community for its sheer depth, raw speed, and advanced toolset. It’s especially popular among CTF (Capture the Flag) players, bug bounty hunters, and security teams looking to customize their toolchains without sacrificing performance.
Other PenTesting OS
Kali Linux
Kali Linux, maintained by Offensive Security, is the most widely recognized Linux distro for penetration testing and offensive security work. Based on Debian, Kali comes with over 600 curated tools for vulnerability assessments, wireless attacks, password cracking, web app testing, social engineering, reverse engineering, and more. Its intuitive GUI, vast community support, and official training resources (like the OSCP certification) make it the default choice for learners and professionals alike.
Kali supports live booting, encrypted persistent storage on USB, and advanced customization through “Kali Metapackages.” It also offers ARM support and virtual machine images preconfigured for VMware and VirtualBox. Whether you’re doing red teaming, bug bounty hunting, or network audits, Kali is the most popular and well-documented toolkit in the cybersecurity world.


Parrot Security OS
Parrot Security OS, developed by Frozenbox, is a Debian-based Linux distro that merges offensive security tools with strong privacy and anonymity features. It includes most of the same tools as Kali, but also comes bundled with privacy-focused software such as AnonSurf, TOR, I2P, and secure communication apps. The OS supports secure development environments, GPG encryption, digital forensics, vulnerability analysis, and exploit development—all while minimizing your digital footprint.
Parrot uses the MATE desktop environment, which is lightweight and user-friendly, and also offers a Home Edition without the security tools for daily private use. It’s a great choice for pentesters, OSINT researchers, digital nomads, and activists who want both hacking tools and robust privacy out of the box.
BackBox Linux
BackBox is an Ubuntu-based penetration testing and security assessment distribution known for its simplicity, speed, and minimalism. While it includes fewer tools than Kali or BlackArch, its focus on stability and usability makes it ideal for quick field deployments or low-resource environments. It covers most key cybersecurity categories including network auditing, application testing, forensics, and exploitation.
BackBox features a clean XFCE desktop, easy-to-navigate menu systems, and well-curated tools that avoid the bloat often found in larger distros. It’s a great solution for cybersecurity professionals who prefer an efficient, fast, and easy-to-maintain pentesting environment without sacrificing effectiveness.


Pentoo Linux
Pentoo is a Gentoo-based live CD built specifically for penetration testing, exploit development, and wireless auditing. It includes a hardened kernel with grsecurity and PAX patches, making it ideal for testing at both the network and kernel level. It supports GPU acceleration (OpenCL, CUDA) for password cracking tools like Hashcat and John the Ripper, and includes specialized wireless tools like Aircrack-ng, Reaver, and Kismet.
What sets Pentoo apart is its Gentoo base, allowing for deep customization, source-based compilation, and performance tuning. It’s a great fit for advanced Linux users, kernel researchers, and wireless security specialists who need a fast, hardened, and customizable distro focused on deep system-level testing.
Caine Linux
CAINE (Computer Aided INvestigative Environment) is a forensics-focused Linux distribution built on Ubuntu and tailored for digital investigations, data recovery, and incident response. It features a complete suite of forensic tools like Autopsy, The Sleuth Kit, Volatility, and ddrescue, as well as GUI-based evidence handling tools and disk imaging utilities.
CAINE is structured to preserve digital evidence—it auto-mounts disks as read-only, provides write-blocking support, and offers logs for chain-of-custody verification. It’s widely used in law enforcement, corporate incident response teams, and academic training environments where digital evidence integrity and compliance are mission-critical.


NST
NST is a Fedora-based distribution designed for network security monitoring, analysis, and traffic diagnostics. Its standout feature is a powerful web-based GUI that provides dashboards and control panels for tools like Snort, Suricata, Nmap, ntopng, Wireshark, and NetFlow. NST is ideal for security operations centers (SOCs), universities, and system administrators managing large-scale or enterprise networks.
NST supports packet capture, real-time flow monitoring, wireless scanning, and network visualization, and can be booted from a live USB or run in a VM. It’s not designed for offensive security or exploit development—NST excels as a network-layer defense and analytics platform, especially for blue teams and forensic analysts.