
Acronis is a leading global technology company that provides comprehensive data protection, backup, disaster recovery, and cybersecurity solutions. Established in 2003 and headquartered in Schaffhausen, Switzerland, the company has grown to serve millions of customers worldwide, offering a wide range of solutions designed to secure, back up, and recover data across various environments and devices.
Acronis specializes in providing robust backup and recovery solutions for both personal and business use. For individual consumers, Acronis True Image is a popular tool that offers disk-imaging capabilities, allowing users to back up their entire system or individual files and easily recover them if needed. The product is available for both Windows and macOS platforms and supports incremental backups, making it a comprehensive data protection tool.
For businesses, Acronis provides scalable and enterprise-level data protection solutions, including Acronis Cyber Protect, which integrates backup, disaster recovery, and cybersecurity into a single platform. This solution is designed to protect against ransomware, malware, and other cyber threats, offering both on-premises and cloud-based backup options. Acronis's cloud solutions are designed for secure, off-site data storage in their geographically distributed data centers, ensuring data is protected from physical damage or theft.
One of Acronis's standout features is its advanced ransomware protection capabilities, which continuously monitor and protect data from ransomware attacks. By integrating cybersecurity with backup solutions, Acronis provides a comprehensive defense against modern threats, ensuring that businesses and individuals can recover their data without paying ransoms.
Additionally, Acronis offers disaster recovery services for businesses to ensure minimal downtime in the event of data loss or system failures. Their solutions are tailored for both small-to-medium businesses (SMBs) and large enterprises, providing centralized management, high scalability, and support for virtual environments, such as VMware, Hyper-V, and other cloud-based infrastructure.
Acronis is widely recognized for its ease of use, fast backup speeds, and reliability in delivering data protection. With millions of users across over 145 countries, it has established itself as a trusted provider in the data protection space, combining powerful backup technology with modern cybersecurity features.
List of Services
-
PhishingItem Link List Item 1
Phishing is one of the most common email-based attacks. Hackers send emails that appear to come from legitimate sources, such as banks, popular services, or colleagues, in order to trick the recipient into revealing personal information. These emails often contain links to fake websites that closely resemble real ones. When users enter sensitive information, such as passwords or credit card numbers, it is captured by the attackers.
Example: An email that seems to be from a bank asking the user to reset their password by clicking on a link.
-
Spear PhishingItem Link List Item 2
Spear phishing is a more targeted form of phishing. Hackers tailor their emails to specific individuals or organizations. This method involves gathering information about the target (e.g., job titles, interests, or social media activity) and crafting an email that looks personalized and trustworthy. Because the message is more relevant to the victim, it increases the likelihood of the target falling for the attack.
Example: A hacker impersonates a company executive and sends a fake email asking an employee to transfer funds or share confidential information.
-
Business Email Compromise (BEC)Item Link List Item 3
Business Email Compromise (BEC) involves hackers gaining access to a company's email account, often through phishing or other social engineering techniques. Once they have access, the hacker can impersonate the CEO, CFO, or another key individual and send emails to employees, requesting financial transactions or the sharing of sensitive data.
Example: A hacker compromises the email account of a CEO and asks the accounting department to wire funds to an overseas bank account.
-
Malware and RansomwareItem Link List Item 4
Hackers may send emails containing attachments or links that, when opened, install malware or ransomware on the victim's device. Malware can steal sensitive information like passwords, while ransomware can lock files and demand payment in exchange for the decryption key.
Example: An email with an attachment disguised as an important document, which, when opened, installs malware to capture keystrokes or passwords.
-
Credentials StuffingItem Link
After obtaining a list of stolen usernames and passwords from data breaches, hackers use credential stuffing attacks to try these credentials on other platforms, such as email accounts. Since many people reuse passwords across multiple sites, hackers may be able to access an individual's email or other accounts if the same credentials are used elsewhere.
Example: A hacker uses stolen login credentials from a previous breach to attempt access to the target's email account or social media accounts.
-
Email SpoofingItem Link
Email spoofing involves forging the "From" address on an email to make it appear as if the message is coming from a trusted source, such as a company or a friend. The hacker may use spoofed emails to convince the target to open malicious attachments or click on phishing links.
Example: An email that appears to be from a friend or coworker asking the recipient to open an attachment or visit a website.
-
KeyloggingItem Link
Hackers may send emails with attachments or links that, when opened, install keyloggers. These malicious programs record every keystroke made on the victim’s device, including passwords and other sensitive information.
-
Social EngineeringItem Link
Hackers use psychological manipulation in emails to trick individuals into taking certain actions, such as providing login credentials or opening attachments. The emails may create a sense of urgency, fear, or trust, such as claiming that an account will be locked unless immediate action is taken.
-
Man-in-the-Middle (MITM) AttacksItem Link
In a MITM attack, hackers intercept email communications when they are sent over unsecured networks (e.g., public Wi-Fi). The attacker can then read, alter, or inject malicious content into the emails, potentially gaining access to sensitive data.
Identity Theft
Acronis Cyber Protect provides robust protection against many of the threats that lead to identity theft. By detecting and blocking malware, ransomware, and phishing attempts in real time, Acronis prevents hackers from stealing personal files, login credentials, and sensitive data stored on your devices. Its integrated backup and secure recovery features also ensure that your information is safe—even if a device is compromised or lost.
However, while Acronis defends your devices and data, it does not offer credit monitoring, SSN activity alerts, dark web scans, or identity recovery services—the specialized tools necessary for full-spectrum identity protection.
For complete coverage, we recommend pairing Acronis with a trusted identity protection service like Aura. Aura offers 24/7 credit and bank account monitoring, identity theft insurance, SSN tracking, and real-time dark web alerts, giving you peace of mind across your entire digital footprint.
Together, Acronis and Aura form a powerful security duo—Acronis protects your devices and data, while Aura protects your identity and financial life.
Anti-Virus
Acronis is considered one of the most advanced and reliable data protection solutions available today because it combines traditional backup services with next-generation cybersecurity features — all in a single unified platform. This approach is especially beneficial for businesses and managed service providers (MSPs) that need to protect endpoints, prevent downtime, and respond to evolving threats in real time.
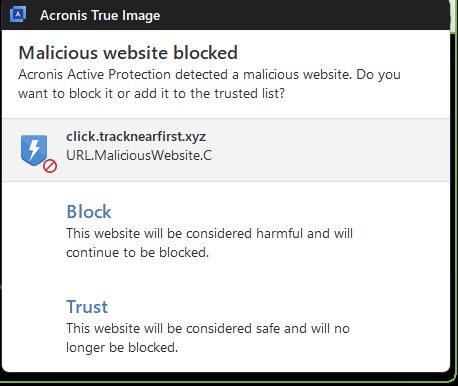
What sets Acronis apart is its ability to not only create secure backups but also actively defend systems against malware, ransomware, and data breaches. Its AI-powered anti-ransomware engine can detect suspicious activity — such as unauthorized encryption — and immediately halt the process while automatically restoring affected files from backup. This feature is particularly effective in protecting against modern ransomware attacks that often target backup files themselves.
Another reason Acronis stands out is its wide support for diverse environments. It can back up and protect Windows, macOS, Linux, iOS, and Android devices, as well as virtual machines, Microsoft 365, and Google Workspace. Whether you're dealing with physical servers, workstations, cloud platforms, or mobile devices, Acronis delivers consistent and centralized protection. The ability to manage everything from one cloud-based dashboard simplifies IT administration, allowing users to schedule backups, monitor antivirus alerts, deploy security updates, and even perform vulnerability scans from a single interface.
One of the most valuable features Acronis offers is its built-in antivirus engine. Unlike standard antivirus software, Acronis’ cybersecurity tools are fully integrated with its backup and disaster recovery functions. This means it can scan data during backup operations, prevent infected files from being stored, and ensure that data restores are clean. Its real-time antivirus system includes behavior-based detection, exploit prevention, web filtering, and full-disk and memory scanning — allowing it to identify threats even before traditional signature databases are updated.
In essence, Acronis provides a comprehensive cyber protection solution that minimizes complexity while maximizing defense. By combining reliable backup with proactive antivirus protection, it helps businesses not only recover from cyber incidents but also prevent them altogether — making it an ideal choice for modern data security and endpoint protection needs.

Contact Us
We will get back to you as soon as possible.
Please try again later.

